By Shanti Terry
Editor’s Note: We share the following as our “Part 2” coverage on the topic of Cyber Security, continuing the conversation that was begun in the September issue, in the article titled “Navigating the Cyber Security World.”
Although gaining more awareness and fully understanding the questions around cyber attacks is vitally important, the information is useless if those in critical infrastructure industries do not take action. With that in mind, we moved on to the task of sharing information about what oil and gas companies can do to protect themselves.
Andrea Little LImbago is principal social scientist at Endgame, a cyber security software company involved in protecting both national security and commercial interests from advanced cyber threats. Last month we shared Limbago’s observations about headline-grabbing cyber attacks, and how these high-profile events steal attention away from lesser-known but more close-to-home events. “At the end of the day, the more worrisome attacks and potential attacks that are being caught are not the ones that are gaining much attention,” said Limbago. “This is especially true of the oil and gas industry specifically. The media reports more on stories that are more sensational, like the breach at Sony.”
What we didn’t share from Limbago last month was her two-step strategy for gaining control of one’s cyber resources.
Step One: Admission
You are a target. Admission is always the first step in any kind of recovery program, and so it goes for companies wanting to recover from leaving themselves open to cyber threats. “A company acknowledging that it is a target is a really big first step,” said Lombago. “So every oil and gas company should view itself as a target, no matter how small they are.”
And it’s more complicated than that.
“Companies involved with the oil and gas industry are targets too, like supply chain companies that provide parts. Attacking a company that does business with oil and gas can be a way in to larger companies.”
Step Two: Strategizing
Data prioritization, segregation, layered security, framework study, and staff training are a few ways of developing a strategy for cyber security that can withstand significant threats. Although nothing is “fail-proof,” implementing these components can make a significant difference in lowering cyber vulnerability.
Data Prioritization and Segregation
Limbago discussed with us the importance of data prioritization as a first step. She shared that, because oil and gas is one of the critical industries that drives the economy, data prioritization is crucial to deciding what information is at risk. To get things started, companies must first ask themselves question like:
What data is most important here?
What’s an idea of a worst-case scenario?
What would happen if that important data were lost?
Once those questions have been answered, it’s time for segregation. “The data needs to be segregated, so that all of their eggs are not in one basket, and if there is a breach, everything isn’t stolen all at once,” said Limbago.
Another source quoted last month, Eddie Block, occupies a special place in Texans’ lives, where cyber security is concerned. Block is the current Chief Information Security Officer and Cyber Security Coordinator at the Texas Department of Information Resources (DIR), and as such he heads an agency that is on the front lines of cyber defense. As Block remarked in Part 1, “One of our goals here, within the state, is to not only collect information, but share it with our public partners. We are trying to develop ways of sharing that information with the private sector partners…. We’re working with a number of our higher risk agencies to make sure that we’re sharing information better and in a more uniform way.”
On the topic of framework study, Eddie Block discussed the cyber security framework that was published by NIST (National Institute of Standards and Technology) last year. He explained that Texas has taken and adapted that framework to be a bit more granular for agency use, but the framework is a great starting point for those structures that want to start trying to identify gaps in their cyber security. “It’s a great way to start to look at how to build a more mature security program,” said Block. “The NIST framework is adaptable to most industries. It was developed for critical infrastructures, so it’s particularly fitting for oil and gas.”
“Layered” Security
Thomas Mandry, CEO of Mandry Technology Solutions, says that companies truly need a layered security approach in order to safeguard themselves.
Mandry Technology Solutions is an MSP (Managed Service Provider) company operating across West Texas, and its CEO attributes the rise of cyber attacks in oil and gas to the industry’s rapid growth. Energy businesses are focused on what they do in their core business. As Mandry remarked in last month’s report, “They do some basics like a standard firewall and antivirus software, but they are still leaving themselves exposed via things like passwords left out on desks on stick notes and passwords that are easy to guess, like family members’ names.”
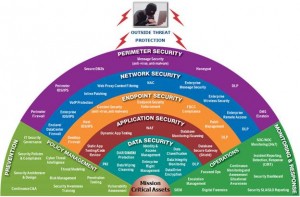
We pick up that thread this month with Mandry’s explanation the basic elements of layered security. He compares the system to home security. When you own a home, you install locks on your doors. For an added measure of protection, you might also install security cameras, an alarm system, and so on. If someone breaks into the house, they must first get through the front door. After that, you have them on camera and you can see them, but you need a system in place for doing something about the intrusion, which is where the home alarm system would come in. Police can be dispatched and things go on from there. With that analogy in mind, here are the levels of layered security:
(1) Perimeter security—It’s generally the first line of defense and contains things like antivirus software and firewall protection. “If you have a commercial grade firewall, you’ll be in great shape,” said Mandry. A lot of people don’t. They have the $99.00 router, which is very easy to hack into compared to a business class one that can do a better job on a cyber attack.”
(2) Network Security—This layer contains web filtering, which keeps employees from being able to visit harmful sites. Mandry said that many companies do not have web filtering, but they should, as it can block many things, like viruses.
(3) End Point Security—This layer entails patch management, which can best be explained as software updates. In order to keep things patched up, updates need to be performed daily.
(4)Application Security—“You can really add levels of security within applications and make those passwords differ from that of the PC. You can monitor who’s coming and going out of applications, like your accounting app.”
(5) Data Security—This layer includes things like travel lap tops and mobile phones, things that can be lost or stolen. According to Mandry, the best way to keep these devices from becoming a way for someone to get in and take information is to make sure they have drive encryption. “If data security is done well, a professional could remote wipe a machine and prevent data theft.”
The last two layers are (6) Policy Management and (7) Operations. Both of these layers contain more of what we’ll call the “human element.” Policy management involves having good written policies for employees that govern and define what is acceptable on the network and what is not. Policy Management also contains penetration testing, which Mandy referred to as white glove hacking. “We’ll do a test and run a scan towards the oil and gas company to see if it’s easy to hack into them and find vulnerabilities.” As for operations, employee training is its core function. “Employees need to know what to do when they receive phishing attacks and get popups on their computers.”
An added thought from Mandry for companies conceiving their cyber security setup was to consider cyber security insurance. “It’s a separate policy that can be bundled onto your general insurance. It covers damage, like hackers breaking in and causing thousands of dollars of damage, deleting data, selling damaging information.”
After prioritizing and segregating one’s data, with all those layers of security in place, one might assume that their cyber security is impenetrable. Unfortunately, that’s not the case. The human element must always be factored into the equation, and it will either be a blessing or a curse.
Shanti Terry has been a freelance writer/blogger since 2011. She can be reached via email at terryamoni@gmail.com.