by Geoff Yut
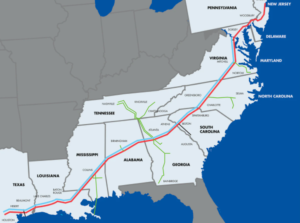
The recent cyberattack on Colonial Pipeline underscores just how vulnerable critical U.S. infrastructure is to cybercriminals. On May 7, 2021, Colonial Pipeline, a major U.S. fuel pipeline operator, halted operations as a precautionary measure after a cyberattack involving ransomware was discovered. The attackers appear to have accessed business systems from which they stole nearly 100 gigabytes of data before they locked Colonial Pipeline’s computers and demanded ransom. Responsible for nearly half of the U.S. East Coast’s fuel supply, Colonial Pipeline supplies fuels from Gulf Coast refining centers to cities, including Washington, D.C., Baltimore, and Atlanta, transporting 2.5 million barrels per day of gasoline, diesel, and jet fuel through 5,500 miles (8,850 km) of pipelines.
The attack represents a major disruption of the U.S. energy sector and is the latest in a string of unsettling cyberattacks by foreign actors that have drawn attention to the need for private companies and government agencies to harden their digital assets.
Threat Actor Profile
According to an FBI statement, the strain of malware involved appears to be the work of a Russian ransomware gang called “DarkSide.” DarkSide operates under a Ransomware-as-a-Service (RaaS) model and, once a system is compromised, cybercriminals using these services can demand anywhere between $200,000 and $2 million.
DarkSide users display comprehensive capabilities across multiple software systems and platforms, collecting information from a variety of private organizations, including financial institutions, medical facilities, energy firms, and tech giants. These types of hackers aren’t worried about avoiding detection; rather these actors employ tactics that aim to leverage a company’s desire to keep the breach quiet to pressure them into paying up. A popular such tactic is called “double extortion,” a technique in which criminals demand that victims pay to decrypt the stolen data and prevent the hackers from leaking sensitive data. This technique allows hackers to increase both the number of ransoms they receive and the value of those demands. Industry observers regard the Colonial Pipeline cybersecurity incident as financially motivated as opposed to state-directed sabotage compared to what had been observed in the SolarWinds or Microsoft Exchange hacks earlier this year.
State Of Security In The Energy Sector
The energy industry is still maneuvering the widespread digital transformation of operational and support structure that gained momentum in recent years. There are exciting developments in operational and information technology for oil and gas applications—many oil and gas companies are prioritizing investments in this area. Two examples of such developments include the Internet of Things (IoT), which facilitates data collection, and Supervisory Control and Data Acquisition (SCADA) systems, which use data to monitor and control facilities located throughout the energy supply chain.
However, these technologies inherently increase an organization’s attack surface, requiring authentication and authorization management between them. Experts predict that the number of connected devices worldwide will reach a whopping 46 billion by 2021—all equipped with sensors that communicate back to networks, databases, and communications systems. These connected devices span a wide range, from smart toasters to centrifuges enriching uranium. Even a fish-tank thermometer can expose firms to trouble from hackers. As mentioned in a recent NSA advisory for stopping malicious activity against connected operational technology (OT), it doesn’t help that many of the “OT assets and control systems installed and used throughout the energy sector are past end-of-life and operated without sufficient resources.” Put simply, these systems are dinosaurs. This means updates and vulnerability patches aren’t being developed, stifling IT teams tasked with defending these legacy systems and opening firms up to a considerable amount of risk.
Additionally, the critical infrastructure that’s the foundation of the end-to-end energy supply chain makes it particularly vulnerable and more
attractive to these state-sponsored groups. This is compounded by the fact that energy remains a major concern for the nation-states who are often enabling these bad actors. The energy sector drives so much policy across the world that it affects how countries conduct themselves and interact. Therefore, nation-states are willing to attempt these sophisticated, large-scale, and long-term campaigns to gain any advantage they can.
Upon final analysis, firms can expect these attacks to become more disruptive and frequent, therefore increasing their exposure and risk. So, what steps can firms take to ensure the safety of their systems, especially within industries like energy that historically underinvest in cybersecurity? Will energy players heed the warning and double down on hardening their assets? How are the different systems widely used by firms, like energy trading and risk management (ETRM) and enterprise resource planning (ERP) systems, affected by cyber threats and what are some strategies in dealing with those effects? What role does in-depth analysis of existing systems play in developing these strategies?
Opportune is well-versed in assisting clients with mitigating cybersecurity events, digital transformation, and business process modeling so organizations can effectively plan for and adapt to new cyber threats and the impact they have on their business.
About The Expert
Geoff Yut is a Consultant in Opportune LLP’s Process & Technology group based in Houston. Geoff graduated from Texas A&M University with a B.S. in Management Information Systems and a minor in Cybersecurity.